Content Security Policy
(2025-11-14T12:12.720Z)
Perplexity Query
(2025-11-14T12:12
.720Z)
Question:
Write a comprehensive one-page article about "Content Security Policy".
Model: sonar-pro
Content Security Policy: Securing Modern Web Applications
Introduction
A Content Security Policy (CSP) is a crucial web security standard designed to prevent and mitigate threats such as Cross-Site Scripting (XSS) and data injection attacks. By providing web developers with control over which content sources are trusted, CSP has become fundamental for protecting sensitive data and user privacy in today’s increasingly complex online landscape.
[x1calk]
[t4dt90]
[axo3bh]
+%26+its+Importance.png)
Main Content
At its core, Content Security Policy is a set of rules defined by a website that instructs the browser on which resources—such as scripts, images, or styles—it can load.
[axo3bh]
[x1calk]
These rules are typically delivered through HTTP headers or meta tags. A CSP restricts resource execution and loading to approved sources, thereby reducing the risk of malicious code being injected and executed on the site.
For example, consider an e-commerce website that processes user payments. By implementing CSP, it can specify that only scripts from its own domain and trusted third-party payment processors are permitted. If an attacker attempts to inject a script from an unauthorized source, the browser will block it, preventing credential theft or data breaches.
[t4dt90]
[bmj5k9]
Common use cases for CSP include:
- Preventing clickjacking by controlling the embedding of web pages.
Benefits of CSP are substantial:
- Regulatory compliance: Supports adherence to industry standards and legal requirements for protecting sensitive information. [axo3bh]
- Adaptability: CSP can be updated promptly to counter emerging threats as the security environment changes. [x1calk]
Challenges include:
- Compatibility issues: Overly restrictive policies may inadvertently block legitimate content, disrupting website functionality. [axo3bh]
- Maintenance: Regular updates to the policy are necessary as website structure and third-party dependencies evolve.
- Best practices suggest rolling out CSP incrementally, with ongoing testing and thorough documentation to ensure both robust security and a positive user experience. [axo3bh]
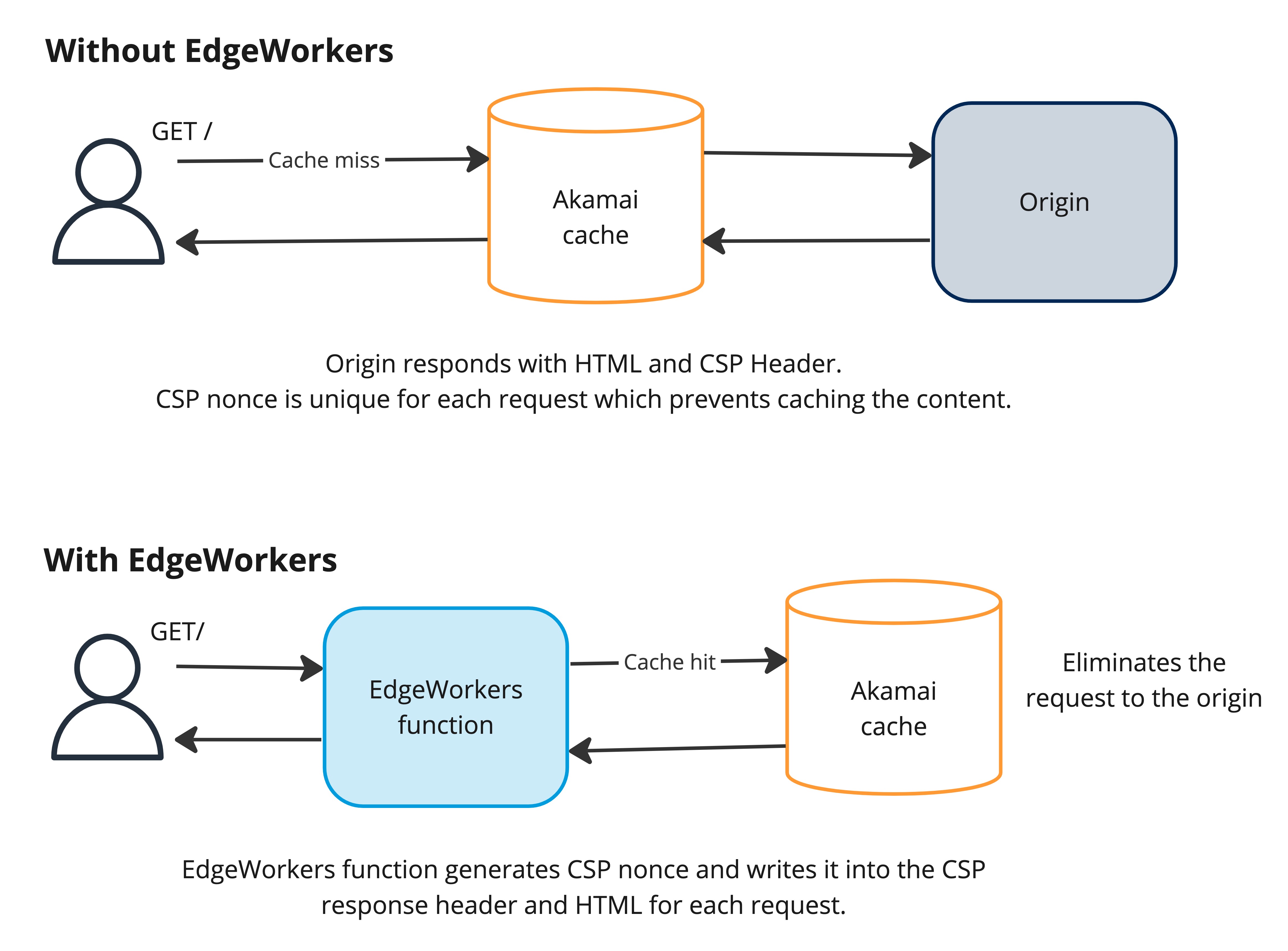
Current State and Trends
CSP adoption is now widespread among security-conscious organizations, especially in sectors handling sensitive data such as finance, e-commerce, and healthcare.
[x1calk]
[axo3bh]
Leading web browsers offer robust support for CSP mechanisms, making it an accessible solution for developers worldwide.
[t4dt90]
[bmj5k9]
[7o3a1d]
Key players in CSP technology include browser vendors (such as Google Chrome, Mozilla Firefox, and Microsoft Edge Browser), as well as commercial security platforms that provide CSP management and monitoring features.
[t4dt90]
[7o3a1d]
Recent developments focus on more granular control—such as per-page or per-module policies—and enhanced reporting to better detect compliance violations and adapt to new attack vectors.
[x1calk]
[t4dt90]
Emerging trends include:
- Integration of CSP with other security headers for layered protection.
- Automation tools that facilitate policy creation, validation, and maintenance.
- Real-time analytics for policy violation reporting and faster incident response.

Future Outlook
Looking ahead, the importance of CSP is set to grow as cyber threats become increasingly sophisticated and the complexity of web applications escalates. We can expect more advanced CSP features, seamless integration with web development frameworks, and tighter coordination with broader security systems. This evolution will further bolster the capacity of organizations to safeguard user data, maintain compliance, and sustain user trust.
Conclusion
Content Security Policy is an indispensable pillar of modern web application security, protecting against common vulnerabilities while fostering user trust and regulatory compliance. Its ongoing development will continue to shape the future of secure and trustworthy digital experiences.
Citations
[x1calk] 2025, Oct 28. Content Security Policies (CSP): Implementation and Benefits - Verpex. Published: 2024-12-23 | Updated: 2025-10-28
[t4dt90] 2025, Nov 08. Content Security Policy (CSP) - Jscrambler. Published: 2004-01-01 | Updated: 2025-11-08
[axo3bh] 2025, Sep 05. Why Content Security Policy (CSP) Implementation is a Must for .... Published: 2024-08-28 | Updated: 2025-09-05
[4]: 2025, Nov 13. What is a Content Security Policy (CSP)? | Feroot. Published: 2025-06-18 | Updated: 2025-11-13
[bmj5k9] 2025, Nov 14. Content security policy | Web Security Academy - PortSwigger. Updated: 2025-11-14
[7o3a1d] 2025, Nov 14. What is Content Security Policy (CSP) | Header Examples - Imperva. Published: 2024-05-07 | Updated: 2025-11-14
[7]: 2025, Jul 16. What is CSP (Content-Security-Policy) and How does it Relate to Qlik?. Published: 2021-09-20 | Updated: 2025-07-16
[8]: 2025, Jul 01. The Effective Guide to Creating a Content Security Policy. Published: 2025-01-01 | Updated: 2025-07-01