Cross-Site Scripting
(2025-10-12T19:12.423Z)
Perplexity Query
(2025-10-12T19:12
.423Z)
Question:
Write a comprehensive one-page article about "Cross-Site Scripting".
Model: sonar-pro
Cross-Site Scripting: A Persistent Web Security Threat
Cross-Site Scripting (XSS) is a Web Security vulnerability that allows attackers to inject malicious scripts into trusted websites, which then execute in the browsers of unsuspecting users. This code injection attack enables adversaries to compromise user interactions with web applications, steal sensitive data, hijack user sessions, and even take complete control of accounts.
[1c8opg]
XSS has emerged as one of the most prevalent security vulnerabilities on the web today, with researchers estimating that as many as 68% of websites may be susceptible to these attacks.
[7rk12o]
The significance of XSS extends beyond technical concerns—it poses serious risks to user privacy, organizational reputation, and the fundamental trust that underpins web-based interactions.
How Cross-Site Scripting Works
XSS attacks exploit the trust relationship between users and websites by manipulating vulnerable web applications to return malicious JavaScript to users.
[1c8opg]
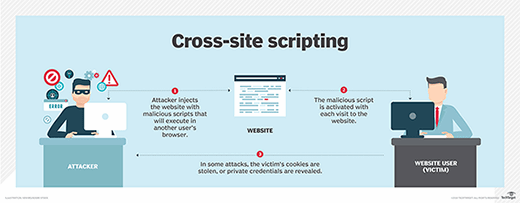
The attack begins when an attacker identifies a web application that fails to properly validate, sanitize, or encode user-supplied input. The malicious code is then injected into the website through various entry points—commonly through URL parameters, form fields, or user-generated content sections like comments and message boards.
[rpnc35]
When other users visit the compromised page, their browsers execute the malicious script as if it came from the trusted website itself.
The fundamental vulnerability stems from how web browsers implement the same-origin policy, a critical security mechanism that grants permissions based on a website's URI scheme, hostname, and port number.
[7rk12o]
When malicious scripts execute within the context of a trusted site, they inherit all the permissions granted to that site. This allows attackers to access sensitive information such as session cookies, authentication tokens, and personal data stored by the browser.
[1c8opg]
The malicious script can perform actions on behalf of the victim user, including reading or modifying page content, capturing keystrokes, and redirecting users to attacker-controlled websites.
[lvjx0l]
A practical example of an XSS attack might look like this: an attacker posts a seemingly innocent comment on a blog that contains hidden JavaScript code. When other users view the page, the script executes automatically in their browsers, sending their session cookies to the attacker's server. The attacker can then use these stolen credentials to impersonate the victims and access their accounts. Web forums, social media platforms, blogs, and any site that displays user-generated content without proper sanitization are particularly vulnerable to these attacks.
[rpnc35]
The Growing Threat Landscape
XSS vulnerabilities have been exploited since the 1990s, but their prevalence and sophistication have increased significantly in recent years.
[7rk12o]
Major platforms including Twitter and Facebook have fallen victim to XSS attacks, demonstrating that even well-resourced organizations struggle with this vulnerability. The term "cross-site scripting" was introduced by Microsoft security engineers in January 2000, and the attack vectors have evolved considerably since then.
[7rk12o]
While JavaScript remains the most common payload, XSS attacks can utilize any client-side language, including HTML, Flash, VBScript, and ActiveX.
The rise of fileless and script-based attacks has made XSS particularly dangerous in the current cybersecurity landscape.
[rpnc35]
These attacks easily circumvent traditional antivirus solutions and firewalls because they exploit legitimate website functionality rather than installing malicious files on victim systems. Cross-site scripting has surpassed buffer overflow attacks to become the most commonly reported security vulnerability.
[7rk12o]
Organizations across all sectors must now incorporate XSS detection and prevention into their comprehensive cybersecurity strategies to protect both their users and their reputations.
Future Outlook and Prevention
The future of web security will require increasingly sophisticated defenses against XSS attacks as web applications become more complex and interactive. Modern security frameworks are evolving to include built-in XSS protection through automatic input validation, output encoding, and Content Security Policy (CSP) implementation. Machine learning and artificial intelligence are being deployed to identify potential XSS vulnerabilities during the development phase, shifting security left in the software development lifecycle. As web technologies continue to advance, the security community must remain vigilant, developing new detection methods and educating developers about secure coding practices.
Cross-Site Scripting remains a critical security challenge that demands ongoing attention from developers, security professionals, and organizations worldwide. As web applications become increasingly central to business operations and daily life, the imperative to eliminate XSS vulnerabilities and protect users from these insidious attacks will only grow stronger.
Citations
[1c8opg] 2025, Oct 12. What is cross-site scripting (XSS) and how to prevent it? - PortSwigger. Published: 2021-07-20 | Updated: 2025-10-12
[rpnc35] 2025, Oct 11. What Is a Cross-Site Scripting (XSS) Attack? - CrowdStrike.com. Published: 2023-05-18 | Updated: 2025-10-11
[7rk12o] 2025, Sep 26. Cross-site scripting - Wikipedia. Published: 2003-06-06 | Updated: 2025-09-26
[4]: 2025, Oct 11. What Is Cross Site Scripting (XSS) and How Does It Work?. Published: 2025-10-03 | Updated: 2025-10-11
[5]: 2025, Aug 06. What is cross-site scripting? - Cloudflare. Published: 2025-01-01 | Updated: 2025-08-06
[6]: 2025, Oct 10. What is Cross Site Scripting (XSS) ? - GeeksforGeeks. Published: 2025-09-23 | Updated: 2025-10-10
[lvjx0l] 2025, Oct 12. Cross Site Scripting (XSS) - OWASP Foundation. Published: 2000-02-01 | Updated: 2025-10-12