End-to-End Encryption
(2025-11-13T21:28.572Z)
Perplexity Query
(2025-11-13T21:28
.572Z)
Question:
Write a comprehensive one-page article about "End-to-End Encryption".
Model: sonar-pro
End-to-End Encryption: Protecting Digital Communications from Start to Finish
End-to-end encryption (E2EE) is a security technique that ensures only the sender and intended recipient can access the transmitted data, shielding information from any intermediaries.
[ki9bhs]
[asbq68]
Its significance lies in safeguarding sensitive communications against unauthorized access, data breaches, and surveillance in an increasingly interconnected world.
[1q8d59]
[3rz2wb]
As reliance on digital communication grows, protecting messages, files, and personal information becomes critical.

Understanding End-to-End Encryption
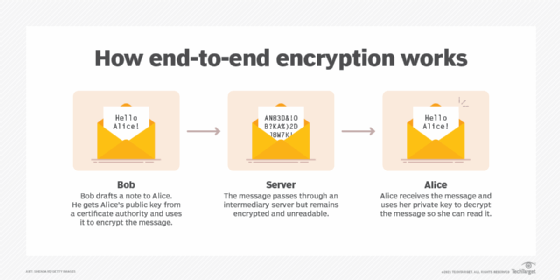
End-to-end encryption works by encrypting data on the sender’s device and only allowing decryption on the recipient’s device, effectively rendering the content unreadable to anyone else—including service providers, internet intermediaries, or hackers.
[ki9bhs]
[k11haa]
Unlike standard encryption that may protect data only in transit, E2EE encapsulates the data from origin to destination, preventing exposure at any point along the journey.
[1q8d59]
The technology typically relies on asymmetric cryptography, utilizing two unique keys—a public key for encrypting and a private key for decrypting—never transmitted together, ensuring only the legitimate recipient holds the means to read the message.
[t4hoa3]
This security method is crucial for protecting communications from being read or altered by third parties.
Practical Examples and Use Cases
Messaging apps such as WhatsApp, Signal, and Apple iMessage have popularized end-to-end encryption by offering private conversations inaccessible even to service providers.
[1q8d59]
[asbq68]
For example:
- Signal: Built from the ground up with E2EE, it allows users to communicate securely.
Other common use cases:
- File storage & transfer: Services like Tresorit and PreVeil employ E2EE to keep documents private from cloud and network attackers. [ki9bhs]
- Telemedicine and remote access, where patient data or confidential business information must remain strictly confidential. [1q8d59]

Benefits and Potential Applications
Key benefits include:
- Protection against surveillance: Prevents governments or malicious actors from intercepting user data. [1q8d59]
- Integrity and authentication: E2EE can incorporate digital signatures and hash functions to verify both message authenticity and integrity. [1q8d59]
- Regulatory compliance: Adhering to privacy laws such as GDPR or HIPAA often requires the high level of security E2EE provides.
Potential applications span secure messaging, email, corporate files, financial data transfers, health records, and more, wherever privacy and data protection are paramount.
Challenges and Considerations
Despite its strength, E2EE faces critical hurdles:
- Key management: Users must securely manage their encryption keys; loss of a private key can mean irrevocable data loss. [ki9bhs]
- Limited server access: Service providers cannot assist in data recovery or moderation since they lack decryption capabilities. [asbq68]
- Regulatory debates: Some governments argue E2EE hampers law enforcement and investigations by making lawful access to communications nearly impossible. [asbq68]
- User experience trade-offs: Integrating E2EE can make apps slightly less convenient, especially with key exchange or recovery processes.
Current State and Trends
Adoption of end-to-end encryption has accelerated in recent years, especially in personal and enterprise communications, driven by privacy concerns and regulatory demands.
[1q8d59]
[asbq68]
Major technology players offering E2EE include WhatsApp, Signal, Apple, and ProtonMail.
[1q8d59]
[asbq68]
Enterprise solutions like PreVeil, Tresorit, and Microsoft’s encrypted messaging for Teams further reinforce the trend in business settings.
[ki9bhs]
Recent developments include:
- Enhancement of protocols (e.g., Signal Protocol integration into new tools).
- Expansion of E2EE to group chats, voice calls, and cloud file storage.
- Debates about “backdoors” and lawful access, as governments pressure tech companies around the world. [asbq68]
Future Outlook
As cyber threats and privacy concerns escalate, end-to-end encryption is expected to become the standard for digital communication. Innovations will likely improve usability, scalability, and interoperability—making E2EE seamless for users and further embedding it into daily life. The ongoing balance between privacy rights and lawful access may shape technological advancement and regulatory frameworks.
End-to-end encryption stands at the heart of protecting digital communication. With continued innovation and widespread adoption, it will help define the future of privacy in a data-driven world.
Citations
[ki9bhs] 2025, Nov 13. End-to-End Encryption (E2EE): What it is & How it Works - PreVeil. Published: 2025-11-11 | Updated: 2025-11-13
[1q8d59] 2025, Nov 10. What is End-to-End Encryption (E2EE) and How Does it Work?. Published: 2025-09-30 | Updated: 2025-11-10
[k11haa] 2025, Nov 13. End-to-End Encryption (E2EE): Definition & Examples | Okta. Published: 2024-09-01 | Updated: 2025-11-13
[asbq68] 2025, Nov 13. End-to-end encryption - Wikipedia. Published: 2004-10-13 | Updated: 2025-11-13
[3rz2wb] 2025, Nov 13. What is End-to-End Encryption (E2EE) and How Does it Work?. Published: 2021-06-25 | Updated: 2025-11-13
[t4hoa3] 2025, Jun 10. What is end-to-end encryption (E2EE)? - Cloudflare. Published: 2025-01-01 | Updated: 2025-06-10
[7]: 2025, Nov 07. What Is End-to-End Encryption & How Does It Work? - Kiteworks. Published: 2024-01-23 | Updated: 2025-11-07
[8]: 2025, Nov 13. A Deep Dive on End-to-End Encryption: How Do Public Key .... Published: 2025-01-01 | Updated: 2025-11-13