API Authentication
(2025-09-24T18:33.964Z)
Perplexity Query
(2025-09-24T18:33
.964Z)
Question:
How does API Authentication work? What are the different kinds of tokens? How do people securely manage their API secrets?
API authentication verifies the identity of the client or user attempting to access an API, ensuring that only authorized parties interact with your application's data and services.
[7nr0ip]
[7n2nud]
It most commonly works by requiring the client to include a credential—such as a token, key, or signed message—within each API request, which the API then validates before granting access.
[7nr0ip]
[7n2nud]
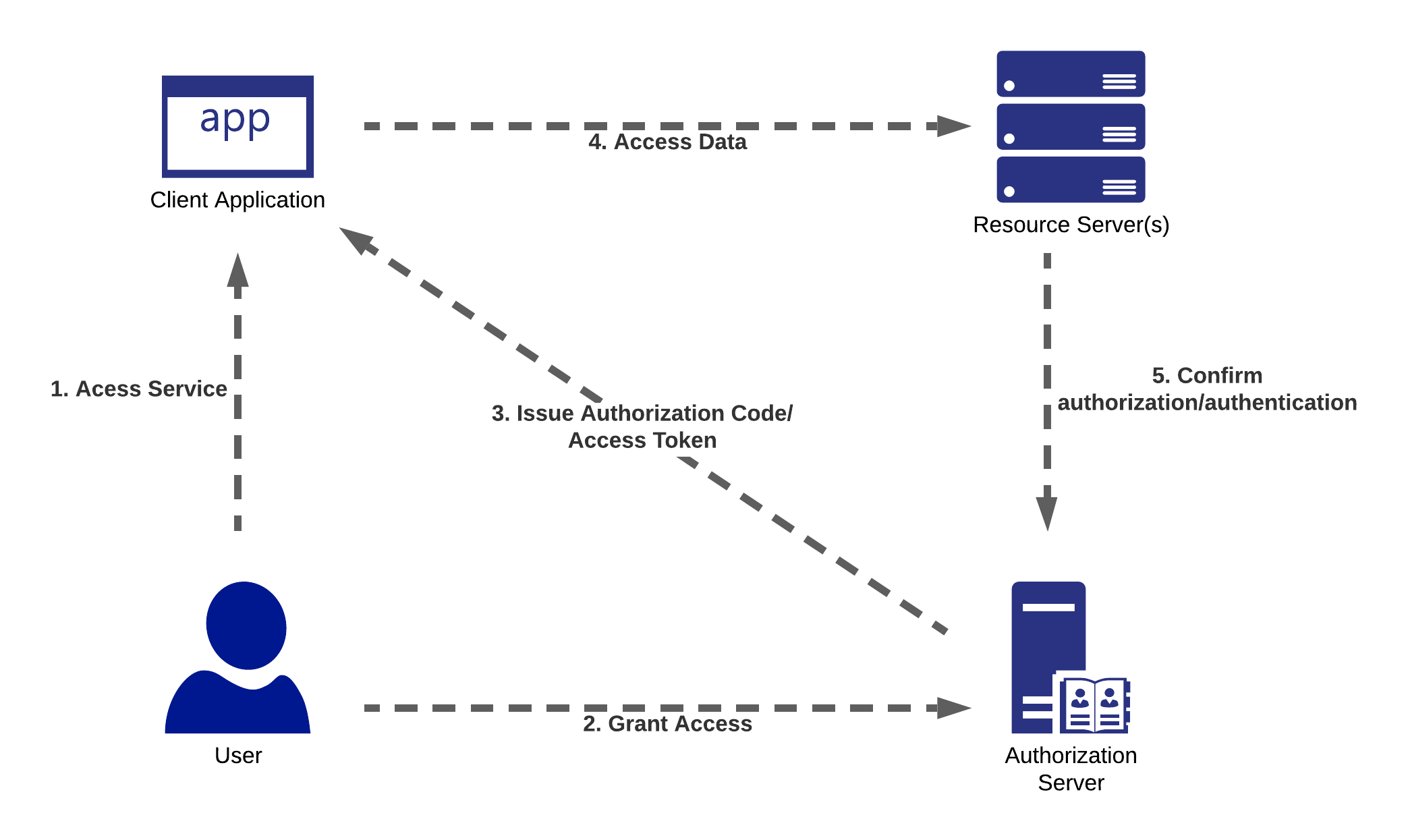

Common API Authentication Methods
- Basic Authentication: The client sends a username and password (usually Base64 encoded) in the request header. This is simple but insecure on its own and should always be combined with HTTPS to prevent interception. [7nr0ip] [7n2nud] Example header:text
Authorization: Basic <Base64EncodedCredentials> - API Keys: A unique identifier (key) is issued to each registered client. The client includes this key in the request (often as a header). It is more secure than Basic Auth, as it doesn't transmit user credentials but does not protect against interception and should be combined with other methods for best results. [7nr0ip] [7n2nud] Example header:text
X-API-Key: <your-api-key> - OAuth 2.0: A more robust framework enabling delegated authorization. The client receives a time-limited access token after an authorization process involving the user and an authorization server. The API validates this token before allowing access. OAuth enables granular permission controls and is widely used for third-party integrations. [7nr0ip] [92dbii] Example token exchange:text
Authorization: Bearer <access_token> - OpenID Connect (OIDC): An identity layer on top of OAuth 2.0, specifically for authenticating users and obtaining ID tokens, commonly used for Single Sign-On (SSO) scenarios. [7nr0ip]
- JWT (JSON Web Token): Often used with OAuth or as a standalone mechanism. JWTs are signed tokens that carry claims (user identity and permissions), allowing stateless authentication. The receiver validates the token's signature and expiry. [7n2nud]
- HMAC (Hash-based Message Authentication Code): The client generates a hash (using a secret key and message) and attaches it to the request. The server recalculates and compares the hash for validation. It is resilient against tampering and replay attacks. [7nr0ip]
- Certificate-based/Auth via mTLS: Mutual TLS requires both client and server to present valid certificates, ensuring the strongest level of assurance for both endpoints. [92dbii]

Types of Tokens
| Token Type | Common Use | Nature |
| API Key | Identify and rate-limit applications | Opaque, unique key |
| Access Token | Short-lived, access to resources (OAuth, JWT) | Often signed (JWT) |
| Refresh Token | Used to obtain new access tokens (OAuth flows) | Long-lived, secret |
| ID Token | User authentication (OIDC) | JWT, contains claims |
| HMAC Signature | Auth/encryption, integrity check | Derived from secret |
Secure Management of API Secrets
- Environment Variables: Store API secrets (keys, tokens) in environment variables on the server, not in code.
- Secret Managers: Use dedicated tools (e.g., AWS Secrets Manager, Azure Key Vault) designed for managing and rotating sensitive data securely.
- Access Control: Limit secret access by using least privilege principles—only necessary services or users should access secrets.
- Rotation & Expiry: Regularly rotate keys and tokens. Set short lifespans for tokens and promptly revoke/replace compromised credentials.
- Never commit secrets to code repositories, and monitor for accidental exposures.
- Encrypt at rest and in transit: Ensure all secrets are encrypted when stored and when transmitted.
Following these practices, along with using strong authentication mechanisms (like OAuth 2.0 with JSON Web Tokens or mTLS where possible), provides robust protection for API endpoints, user data, and application integrity.
[7n2nud]
[92dbii]
Citations
[7nr0ip] 2025, Sep 24. API Auth: Authentication Methods and Examples - Apideck. Published: 2025-09-24 | Updated: 2025-09-24
[7n2nud] 2025, Aug 29. API Authentication: Methods, Best Practices & Security Tools. Published: 2025-03-13 | Updated: 2025-08-29
[92dbii] 2025, Sep 23. Authentication and authorization to APIs in Azure API Management. Published: 2023-11-15 | Updated: 2025-09-23
[4]: 2025, Sep 24. What Is API Authentication? Benefits, Methods & Best Practices. Updated: 2025-09-24
[5]: 2025, Sep 24. Common REST API Authentication Methods Explained - Swimlane. Published: 2021-04-21 | Updated: 2025-09-24
[6]: 2025, Sep 24. EP91: REST API Authentication Methods - ByteByteGo Newsletter. Published: 2023-12-23 | Updated: 2025-09-24
[7]: 2025, Sep 24. Authentication methods and features - Microsoft Entra ID. Published: 2025-03-04 | Updated: 2025-09-24
[8]: 2025, May 04. REST API Authentication Methods.pdf | Internet - Slideshare. Published: 2023-02-08 | Updated: 2025-05-04